CryptoLocker Has A Competitor That Is Worse: CryptoDefense

This is a rare Cyberheist NewsFlash that we send out when we run into something important enough to alert you about right away. Please forward this to your friends and colleagues.
More data became available since the first time I reported on this, so here is a more in-depth warning about new very nasty ransomware.
As we said before, there is furious competition between cybergangs. Late February 2014, a CryptoLocker ransomware copycat competitor called CryptoDefense was released which outdoes the original.
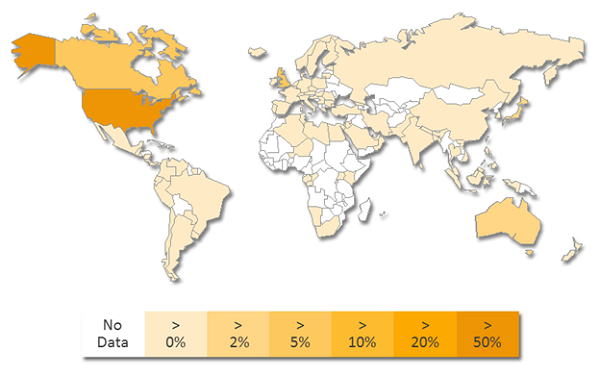
They did their test-marketing in many other countries like the UK, Canada, Australia and others. They are now targeting the U.S. as you can see in this infection heatmap picture generated by Symantec. They are making tens of thousands of dollars per month with this technically sophisticated scam.
If an end-user opens the infected attachment, the CryptoDefense ransomware encrypts its target files, and the criminals charge approx. $U.S. 500 in Bitcoin to decrypt the files. If their four-day deadline passes by, the amount goes to about $U.S. 1,000. Note that Bitcoin exchange rates vary so these numbers are ballpark, and that CryptoDefense is much more expensive to unlock than CryptoLocker.
The ransomware target files are text, picture, video, PDF and MS Office files and CryptoDefense encrypts these with a strong RSA-2048 key which is hard to undo. To add insult to injury, it wipes out all Shadow Volume Copies. Instructions with the ransom demands are added to every folder containing encrypted files. This stinks.
When the hapless end-user clicks the attachment, CryptoDefense connects to four remote domains and sends basic information about the infected workstation. Then, the files on the end-user machine are encrypted, and the private key is sent back to the Control & Command server.
Last, the malware makes a screenshot of the active screen of the end-user workstation and uploads this to their C&C server. That screenshot appears on the payment page where the victim can upload the Bitcoin payments. To reach this page you first need to install the Tor Browser as the payment page is only available via the Tor network, which helps the criminals hide from the law to some degree.
This new CryptoDefense ransomware does not seem to be a derivative of CryptoLocker as the code is completely different, confirming this is a competing criminal gang. Malware has bugs too, and the Symantec researchers wrote: "Due to the attackers poor implementation of the cryptographic functionality they have, quite literally, left their hostages a key to escape". But by the time you read this, the hackers said "Spasiba Symantec" ("Thank You" in Russian) and that bug has been fixed.
RANSOM
CryptoDefense Ransom ScreenIf the victim does not pay within a month, the private key of the encrypted files will be deleted so that access to the encrypted files is no longer possible. They are using RSA-2048 encryption using Microsoft’s own cryptographic infrastructure and Windows APIs to perform the key generation before sending it back in plain text to the attacker’s server. Getting the files back is very hard if you do not have recent backups (made without using Shadow Volume copies).
INFECTION VECTOR
It appears that this infection initially was installed through programs that pretend to be flash updates or video players required to view an online video, and then moved on to a variety of different phishing attacks that all show an email with a zip file and ask to "open the attached document" with is supposed to have been "scanned and sent to you".
PAYMENT ADDRESSES
CryptoDefense allows you to pay the ransom by sending Bitcoins to an address shown in the malware's Decrypt Service page. Often people wind up paying the Bitcoins, as they find their backups could not be restored for a variety of reasons.
It is obvious that this again is a social engineering play and that effective security awareness training will prevent your end-users from opening these infected attachments when they make it through the filters (which they regularly do).
Once infected, the only way to fix this relatively fast is to make sure you have a recent backup of the files which actually can be restored. Wipe and rebuild the machine from scratch, and restore the files. We see an average of three hours of admin work for this.
Recent ransomware infections were users opening an attachment with a "voice mail message" from AT&T, but there are variants from other Telco companies. Users then admit to opening the attachment but saying it did nothing, however they could not open their files afterward.
STOP FILES FROM BEING "RANSOMWARED"
Like we said, make sure your daily backups can be restored. And training your end-users to prevent fires like this is a must these days. So, go to the KnowBe4 website and get a quote for the amount of users in your organization. Do it now, before a user gets social engineered and their files are "ransomwared"



Comment